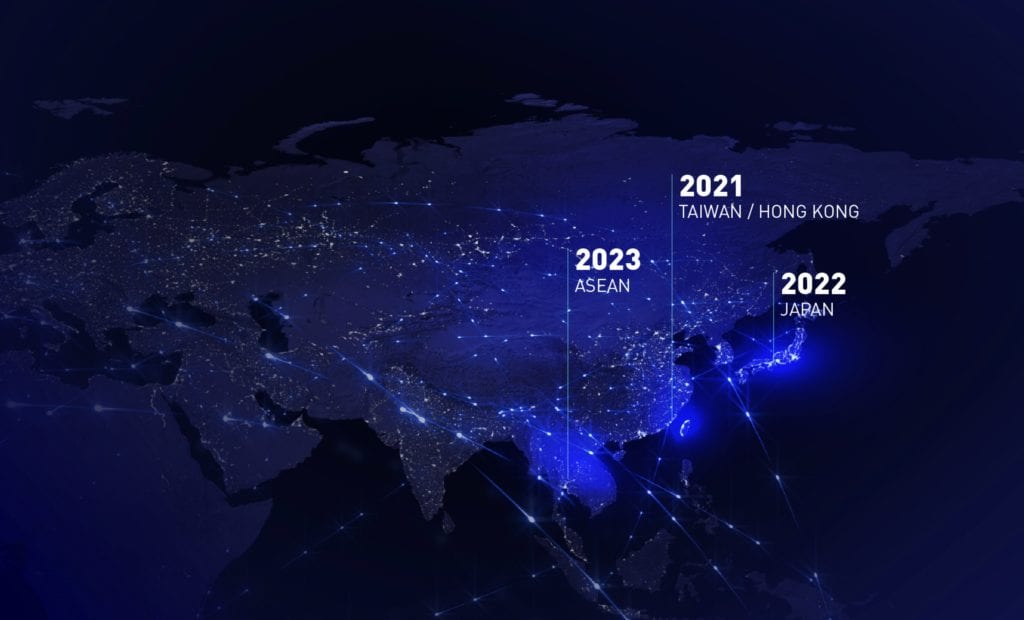
Taiwan (2021)
.ETC Highway RSUs
.Intelligent Science Park & AI Park
.Smart City Infrastructure
.Smart Lampposts
.Smart Medical Devices
Hong Kong (2021)
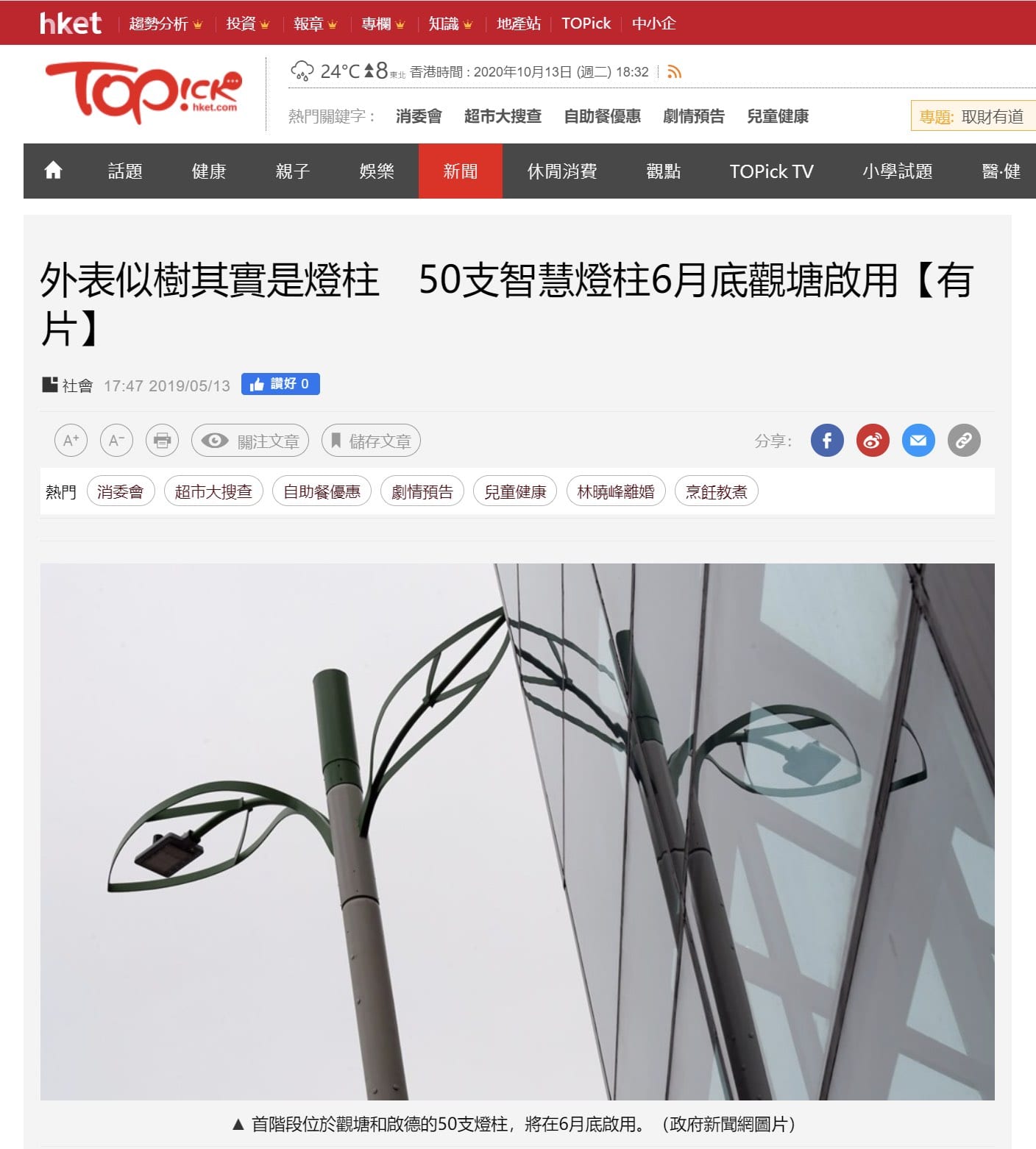
.Smart Lampposts
.Digital Highways
Basic Features
FW & SW Secure Boot
VM & Container Support
Advantages
Suit for Private Systems
Automated Operation
Cloud Native Operation
Private OTA Update
Additional Features
T-REE
Container Notary
Advantages
Suit for Open Systems
Trusted Operation
Trusted App Download
Secure OTA Update
Additional Features
Information Isolation
Trusted Transactions
Advantages
Suit for Info Sensitive App
Raw Data Privacy
Data Monetization


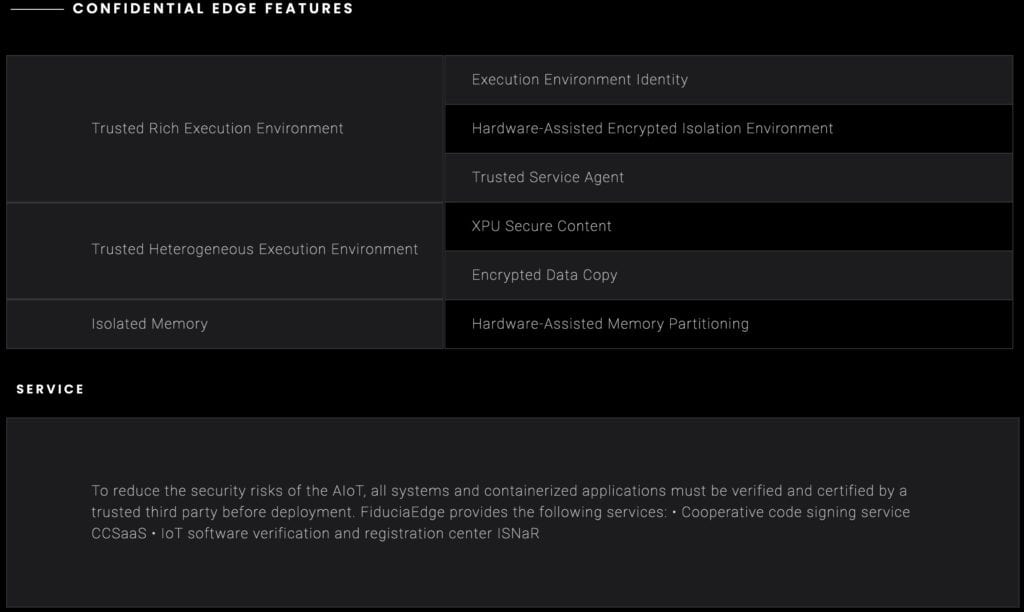
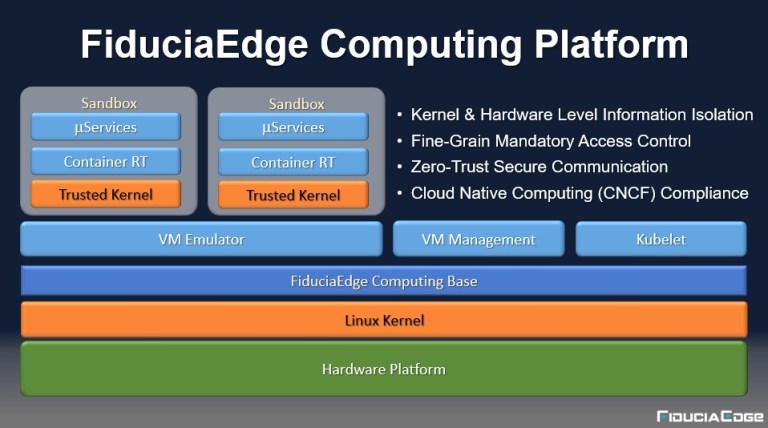
Fiduciaedge committed to providing trusted edge computing platform designed for edge computing nodes, building an ecosystem not only allows data, AI algorithms, and applications to be secured but also protect data privacy at the source.




| Sales Model | Target Customer | Detail |
|---|---|---|
| System Integration | System integrators | For SI who are looking for trust edge computing total solution, we not only have software tech but also great partners who product excellent edge hardware, together we can offer the best solution on the market so far. |
| Software License | AI companies/ Edge device owners | For those who already had edge devices without trust computing function, we can license our software if the hardware was supported. |
| Bundle Selling on branded edge devices | Edge device manufacturers | We provide our trust computing firmware which can embed to their edge device and become a total solution for their customers. |
| Sales Model | Target Customer | Detail |
|---|---|---|
| CCSaaS Service | IPC and ICT equipment suppliers with manufacturing technology/system integrators and operators with secure OTA updates (such as TelCo and ISP) | Provide CCSaaS service for the system software of the device to be developed to ensure the security and correctness of the system and prevent IoT devices from discovering security vulnerabilities or malicious behaviors after deployment; at the same time, provide CCSaaS services for deployed IoT devices to ensure system updates the correctness and safety of the system. |
| ISN&R Platform | Application provider (for example: Industrial Technology Research Institute, National Taiwan University, Jiaotong University AI Center, etc.) / service provider (for example: ITS system integrator and operator) |
.The ISN&N platform performs security checks and endorsements for users and applications, and provides management tools and services such as OTA maintenance, update, and debugging for program developers, and charges users membership fees. .When a program developer performs an OTA update and other operations for an application that has been deployed on an IoT device, it must go through ISN&R to re-verify and register to ensure the security of the new program and update files. .The ISN&R platform can match transactions between users of different levels on the platform (such as the match between IoT hardware vendors and application developers), and extract 5%-30% of the transaction amount. |
Fiducia will be the market leader on solution offerings in compliance of IEEE industrial standards of 1934/1935 and others for the demands in:
Taiwan (2021)
.ETC Highway RSUs
.Intelligent Science Park & AI Park
.Smart City Infrastructure
.Smart Lampposts
.Smart Medical Devices
Hong Kong (2021)
.Smart Lampposts
.Digital Highways
Involvement in Standard Development Organizations (SDO) and Industrial Consortia
Leading Technology Development and Early Adoption
Standard Development Organizatons (SDO)




Processing data locally using edge devices and servers distributes power across a network and reduces bandwidth requirements at central locations. With less need for large onsite data centers or extensive server equipment, businesses can reduce power consumption and cut IT costs. Companies providing streaming services and other content to users of connected devices can also benefit by caching data closer to their customers, which allows for faster delivery and a better overall experience.
Any network in which edge computing is a major player must be maintained in a unified manner to ensure all devices receive regular updates and proper security protocols are followed. Encryption, patching and the use of artificial intelligence to monitor for, detect and respond to potential threats are all essential, and the responsibility for implementing these security measures falls squarely on companies, not end users.
Security agents, devices designed to handle the security measures of which IoT devices are incapable, may provide another solution. This allows security to be undertaken at a network level without sending data all the way to a central server or requiring frequent device upgrades. Security agents are installed near IoT components and function separately to provide the computing power necessary to handle cryptographic security and ensure strong protection against malicious activities.